
السلام عليكم
العدد الاسبوعى من اصدار مجلة كاتازين لايف
- SCTP By Saad Talaat.
- Windows Sins By Alaa Agwa .
- Go!! By Ramzy Kandiel .
- Top 10 Ways To Protect Yourself From Computer Viruses By Khaled Sultan.

السلام عليكم
العدد الاسبوعى من اصدار مجلة كاتازين لايف
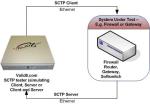
The SCTP is a 11 years old protocol which have been standarized on 2000.
SCTP is reliabe, message-oriented and provides multiple streams.the SCTP almost has the same functionality that the TCP do in it’s one-to-one interface, the one-to-many interface of the SCTP allows trivial porting of the application and some more advanced features unlike one-to-one interface.
so it’s prefered to use the one-to-many interface.
unlike TCP. SCTP is message oriented. it provides sequenced delivery of sequenced records like UDP.
SCTP can provide multiple streams between connection endpoints. each stream has it’s own sequenced delivery messages.
SCTP provides multihoming which means that a single SCTP endpoint can support multiple IP addresses. which means that SCTP can override a network failure by switching to another address which is already associated with the SCTP.
we mentioned before that SCTP is message-oriented.but it’s connection-oriented just like TCP too, but unlike the TCP connection establishment which is three way handshake. SCTP connection establishment is four-way handshake.
You might think that the number is the issue (3 or 4) but the SCTP handshakes are different from the TCP handshakes.
Here goes the scenario :-
1 – server must be ready to accept a connection by supporting a socket and calling bind and listen
2- the client calls connect or sends a message to the server. this makes this client sends it’s list of IP addresses,ISN, number of streams client requests( this is called INIT message )
3- the server ACK the client INIT message with sending INIT,ACK which has the server IP list…etc(like the client) + the state cookie which is a cookie contains all of the stat that the server need to ensure.
4- the client ECHO the cookie with COOKIE-ECHO message
5- the server ACK the validity of that cookie by sending a COOKIE-ACK message
This figure illustrate the 4-way handshake process using 4 packets

But always remember that the SCTP doesn’t have to go into connection establishment to send and receive data. SCTP can be connection oriented or message oriented(connectionless like UDP).
the SCTP interface models as I mentioned above there are two interface models one-to-one,one-to-many. one-to-one interface can correspond to only and only one endpoint. but one-to-many can correspond to many endpoints from one server.
The One-to-One Style :-
this style provides the same functionality the TCP has. what happens in the one to one style is:-
server starts(calls socket,bind,listen),client starts(calls socket,connect). now we have a byte stream between these two points and they exchange data and close connection. so here the server can’t associate many connections at a time because it’s already connected to a point

the One-To-Many style :-
the one to many have several merits. best of them is that an SCTP one-to-many endpoint that can write a server without without managing a large number of sockets. one socket is enough…just like UDP!

What happens here is that the server starts create a socket and bind and listen and then waits for a message.(this blocks till a message arrives),client starts and calls a socket and sends a message and does the four way handshake, server receives the message and sends back a reply..etc and then they both close the socket…enough for today 🙂


Google Introduces ‘Go’ Programming Language
Go is new open source programming language
Rob Pike, a principal engineer at Google said “I’ve never felt as productive as I have working with Go”
Pike says Go’s goal is to serve as a systems language, in the way that C++ or C does today
“It’s fast for development but it also is a true compiled language,” he explained. “We’re opening sourcing it now because we think it’s reached the point of being fun and useful and powerful.”
#history
How did we get here?
1) C and Unix became dominant in research.
2) The desire for a higher-level language led to C++, which grafted the Simula style of object-oriented
programming onto C. It was a poor fit but since it compiled to C it brought high-level programming to Unix.
3) C++ became the language of choice in parts of industry and in many research universities.
4) Java arose as a clearer, stripped-down C++.
5) By the late 1990s, a teaching language was needed that seemed relevant, and Java was chosen.
#reaction
*A number of successful simpler languages (Python, Ruby, Lua, JavaScript, Erlang, …) have become popular, in part as a rejection of the standard languages.
*Some beautiful and rigorous languages designed by domain experts (Scala, Haskell, …) have also arisen, although they are not as widely adopted.
*The standard languages (Java, C++) are statically typed.
*Most outsider languages (Ruby, Python, JavaScript) are interpreted and dynamically typed.
*Perhaps as a result, non-expert programmers have confused “ease of use” with interpretation and dynamic typing.
*This confusion arose because of how we got here: grafting an orthodoxy onto a language that couldn’t support it cleanly.
#the good
* The standard languages are very strong: type-safe, effective, efficient.
* In the hands of experts, they are great.
* Huge systems and huge companies are built on them.
* In practice they work well for large scale programming: big programs, many programmers.
#The bad
* The standard languages are hard to use.
* Compilers are slow and fussy. Binaries are huge.
* Effective work needs language-aware tools, distributed compilation farms, …
* Many programmers prefer to avoid them.
* The languages are at least 10 years old and poorly adapted
to the current computing environment: clouds of networked
multi-core CPUs.
(:(:(:(:(:(:(:Python:):):):):):):)
This is partly why Python have become so popular:
They don’t have much of the “bad”.
– dynamically typed (fewer noisy keystrokes)
– interpreted (no compiler to wait for)
– good tools (interpreters make things easier)
But they also don’t have the “good”:
– slow
– not type-safe (static errors occur at runtime)
– very poor at scale
And they’re also not very modern.
#There is a niche to be filled: a language that has the good,
avoids the bad, and is suitable to modern computing infrastructure:
* comprehensible
* statically typed
* light on the page
* fast to work in
* scales well
* doesn’t require tools, but supports them well
* good at networking and multiprocessing

Go is different
* Go is object-oriented not type-oriented
-inheritance is not primary
-methods on any type, but no classes or subclasses
* Go is (mostly) implicit not explicit types are inferred not declared
objects have interfaces but they are derived, not specified
*Go is concurrent not parallel
intended for program structure, not max performance
but still can keep all the cores humming nicely
… and many programs are more nicely expressed with
concurrent ideas even if not parallel at all
# compiler
* The language is designed and usable. Two compiler suites: Gc, written in C, generates OK code very quickly.
– unusual design based on the Plan 9 compiler suite Gccgo, written in C++, generates good code more slowly
Libraries good and growing, but some pieces are still preliminary
# Testimonials
“I have reimplemented a networking project from Scala to Go. Scala code is 6000 lines. Go is about 3000. Even though Go does not have the power of abbreviation, the flexible type system seems to out-run Scala when the programs start getting longer. Hence, Go produces much shorter code asymptotically.”
–Petar Maymounkov (PhD candidate at MIT, Computer Science and Artificial Intelligence Lab)
“Go is unique because of the set of things it does well. It has areas for improvement, but for my needs it is the best match I’ve found when compared to: C, C++, Erlang, Python, Ruby, C#, D, Java, and Scala.”
–Hans Stimer
Another Go at Language Design

Yes … it has a lot of sins as it is a product of Microsoft .
Microsoft releases closed source products – like windows 7 – which means that users can’t modify , share or examine how it works inside .
i’ll tell you some examples of abuse committed by Microsoft :
This is a brief of what Microsoft do .
After reading this , still want to be a Windows user ?!!

It`s only a matter of time before you encounter a computer viruses , there are top10 steps to protect you from computer viruses :
1) Use a high quality anti-virus program :There are many different
anti-virus computers programs , some of them are better than others , you can find the one that is suitable for your needs by searching on different websites .
2) Always use your anti-virus program : Make sure your anti-virus
program is always turned on and scanning all email messages (incoming &outgoing ) and any software program you run .
3) Keep your anti-virus programs up to date : Most programs
come with a yearly subscription , make sure you take the advantages of the updates , most advanced programs allow you to schedule updates .
4) Keep your computer up to date : From time to time operating system badly affected by the security holes or updates , make sure that you check periodically in order to make sure you are running up to date versions of your software .
5) Backup your data regularly : Most computer users keep
their documents in the “my documents“ folder , this make it easy to back up all of your important documents , you can also copy them to CD or USB drives weekly or monthly .
6) If you use USB drives on public computers like your university
computer lab : Make sure you scan them for viruses , public computers are not being up to date and properly protected .
7) Be careful of email attachments : Treat any email attachment as
may be dangerous , never open attachments from people you weren’t expecting , also be careful of attachments from people you know but weren’t expecting .
8) Use text email if possible : While HTML email is better and
allows you more control over formatting , it also can carry computer viruses , if you use text email the only way to get a virus is by opening an attachment .
9) Use downloading freeware and shareware files or software carefully :
Try to download them from popular trusted sources that scan the programs before they are uploaded , to make sure that you are safe , scan the
program before you install it on your computer .
10) Be careful of links in instant messaging software you don`t
know and never click a link from someone you don’t trust , they can easily redirect you to another website that will try to install a virus on your computer system .